
Kali Linux, LiveCD, VM Images, etc., providing Linux loaded with security testing tools.
Sidebar re: whether all Chip’d cards include RFID (I don’t believe they do).
Ransomeware, malicious software that tries to “monetize the attack” by requesting payment to decrypt hijacked files.
Safe Harbor, an agreement which allowed for data to be stored for customers across different countries which had equivalent data protection regimes.
rot13: “Secret Decoder Ring” with a 13-character shift.
Brute force: we assume an adversary like “Eve” who has the ability to monitor communications always has an attack such that she can attempt all possible decryptions across the entire key space. This is not efficient or cost-effective for the adversary.
Encode vs Encrypt: URL Encoding, Base64, and more… how to tell this isn’t encryption? There’s no “key”.
Imitation Game, recent movie about Alun Turing and the attempts to crack the Enigma machine during WWII.
Apps for encrypted communications: Facebook’s WhatsApp, OWS Signal, TOR, Threema (new to me), …
Data in Transit, Data at Rest: may have different security requirements. Data at rest may be expensive to re-encrypt, and need to remain secure for longer.
Don’t collect what you can’t protect, my advice start-ups trying to figure out what customer data to retain.
Key-wrapping example: There’s a key to encrypt the disk of a multi-user system. Where’s the key? How does each user get the key when they login? Key wrapping! The key that decrypts the disk can be wrapped separately under a key for each user. That way each of them can decrypt the encryption key, then decrypt the drive.
Magic Lantern: how did the FBI deal with getting evidence from suspects who were using strong encryption? Brute-force the key? No, instead they installed a key-logger on the suspect’s machine to capture the password / decryption key before seizing the encrypted disks.
PBKDF2, a mechanism for converting a user-specified password into something suitable as a strong encryption key.
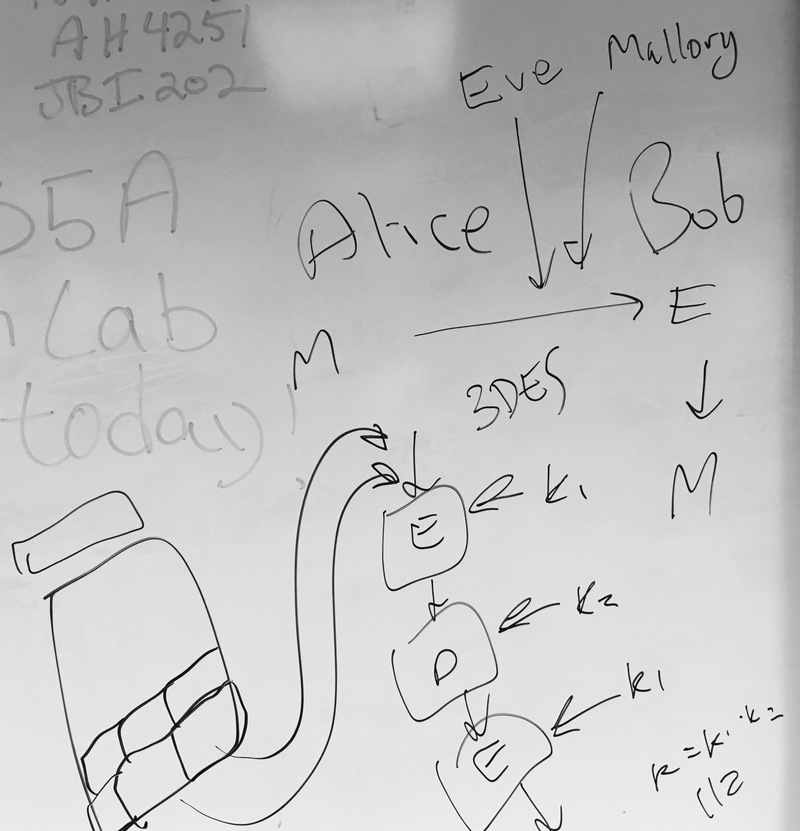
Alice and Bob, our characters who want to communicate securely, and Eve and Mallory, our adversaries who have capabilities that allow them to eavesdrop on (monitor) and perform malicious modification to traffic between the two, respectively.
3DES is a way to take DES and address the problem of having too small a keyspace by performing multiple rounds. DES has 64-but-really-56-bit keys, but 3DES can be used to provide 112- or 168-bit keys.

HSTS, Preload, and HPKP / Pinning are different mechanisms that provide hints from a server to a browser (well, actually that ship with the browser in the case of Preload) to strengthen the guarantees of TLS. Wikipedia helpfully points out that my calling HPKP “certificate pinning” is a misnomer.
