Malware infects apps via developer tools
Insider trading by hacking law firms
Classmate mentions the Ashley Madison Breach
Bill mentions the RSA Breach: RSA Anatomy of an Attack
Cyber kill chain:
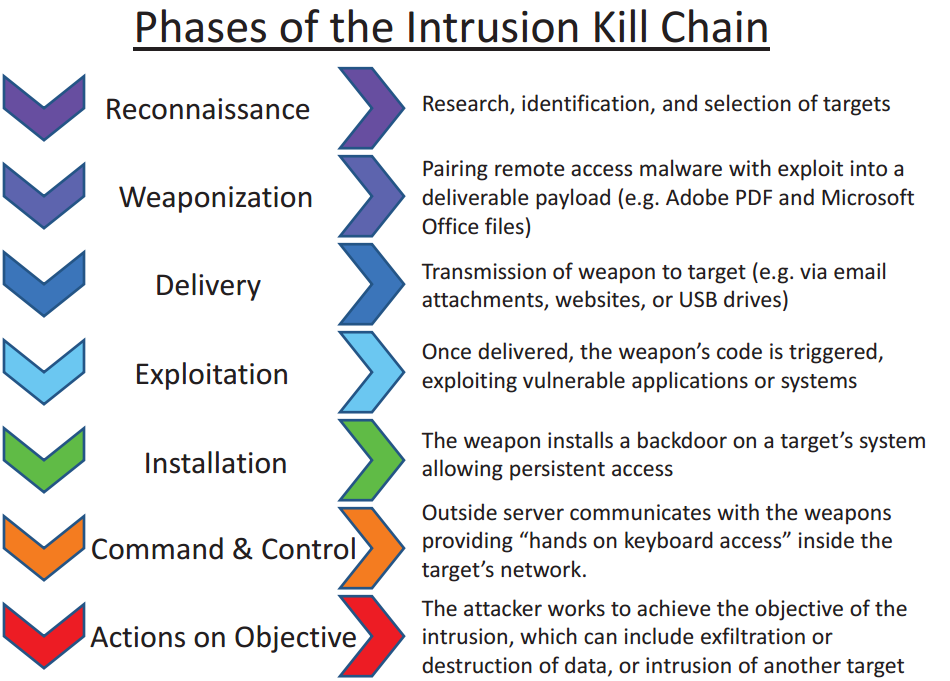
“Kill chain” sounds ominous, “originally used as a military concept related to the structure of an attack”. Bill mentions others that have been re-purposed for cybersecurity, including DMZ. Firewall came from the barrier between the (dangerous) steam engine and the people in a the locomotive.
Viruses and worms seem to have a more organic origin. We have anti-virus, but no innoculation (or is that what patching is?)
Funny to think what names could have stuck, e.g., “web application stockade“
Question from a classmate: How to get into cybersecurity?
- Knowledge of basics – take this class :-)
- Certifications
- Experience from other domains, two popular routes: infrastructure (networking or sysadmin) or application dev
Where do Mac addresses come from? Who gives out OUIs? IANA
What applications that run over HTTP? Lots of things can be tunneled over HTTP, but most common might be things like RDP (which has its own native remote desktop protocol).

HPKP and HSTS are trust-on-first-use (TOFU) headers sent by servers to “modern” web browsers that understand them to signal certain security behaviors. I made some snarky comments about the “preload” form of this same data that ships with Chrome. More secure perhaps but doesn’t seem like a great approach to ship static data like this. Get your own domain listed!
Be aware that inclusion in the preload list cannot easily be undone. Domains can be removed, but it takes months for a change to reach users with a Chrome update and we cannot make guarantees about other browsers. Don’t request inclusion unless you’re sure that you can support HTTPS for your entire site and all its subdomains the long term.
We got to talking about WebSockets and whether they played nicely with firewalls. A classmate mentions that WebSockets could be used by advertisers to get around standard ad blockers (thread on Chrome-dev)
Question from a classmate: TCP/IP network handling – what’s handled in user space, what’s kernel space?
A good article on the topic is Cloudflare’s Why we use the Linux kernel’s TCP stack, which gives an “it depends” answer,
The latency is very important for the HFT (high frequency trading) folks. Traders can afford custom hardware and fancy proprietary network stacks.
In a side discussion, the question was motivated by thinking of attacks that could be triggered via crafted packets that could exploit the kernel directly. I like the way you think! This should be a fairly straight-forward “unpacking” of ones and zeros from the received network traffic, while keeping a small amount of state off to the side before handling the data off to an application in user-space for heavier processing.
One bit of code that parses network traffic are the packet dissectors we saw in Wireshark in the class. Each year there are dozens of security issues reported in these dissectors, usually resulting in some denial of service (affecting only the Wireshark application) if its run against a payload with a specially crafted packet.

I like the first four chapters of High Performance Browser Networking (free online) for “Networking 101”.

Flows through a firewall, permitted in one direction (“outbound to an HTTP server on port 80/TCP”), with the firewall “remembering” state to permit the response traffic back from the web server to the ephemeral port on the client without needing a static rule.
The OSI model vs real-world protocols. Diversity on the top and bottom, TCP/IP in the middle.
Not sure why but we were talking about the Unix Haters Handbook (free online) at some point in the back of the class.
You know the real trouble with Unix? The real trouble is that it became so popular. It wasn’t meant to be popular. It was meant for a few folks working away in their labs, using Digital Equipment Corporation’s old PDP-11 computer. I used to have one of those. A comfortable, room-sized machine.
